Overview of 2024 CVE with CVSS Score 10
Overview of 2024 CVEs with CVSS Score 10
Introduction to CVEs and CVSS
What is a CVE?
A Common Vulnerabilities and Exposures (CVE) is a reference system used to identify and catalog security vulnerabilities in software and hardware. Managed by MITRE, the CVE system provides a standardized identifier for each security issue. Organizations use these identifiers to stay informed about known vulnerabilities, enabling them to protect their systems proactively. Keywords: CVE, CVSS Score 10, cybersecurity, vulnerabilities, risk assessment, enterprise security, web applications, IoT security, Common Vulnerabilities and Exposures, vulnerability identification, Hyper ICT. CVE with CVSS Score 10
Understanding the CVSS Scoring System
Keywords: CVSS, Common Vulnerability Scoring System, risk assessment, vulnerability severity
The Common Vulnerability Scoring System (CVSS) quantifies the severity of a vulnerability. This system considers various factors, including how easily an attacker can exploit the vulnerability, the potential impact on confidentiality, integrity, and availability, and the complexity required to execute the attack. CVSS scores range from 0 to 10, with 10 representing the highest level of severity.
Why Focus on CVEs with a CVSS Score of 10?
Keywords: CVSS Score 10, critical vulnerabilities, cybersecurity threats
A CVSS score of 10 indicates a critical vulnerability. These vulnerabilities pose the highest risk and can lead to significant damage if exploited. Organizations must prioritize addressing these vulnerabilities to prevent catastrophic security incidents.
Overview of 2024 CVEs with CVSS Score 10
Distribution of CVEs Across Different Sectors
Keywords: CVE distribution, sector analysis, cybersecurity landscape
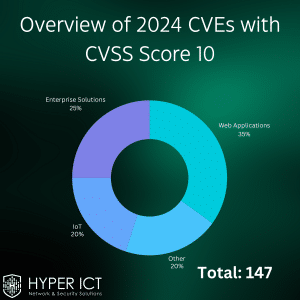
In 2024, the CVEs with a CVSS score of 10 impacted various sectors, including web applications, enterprise solutions, IoT devices, and others. Understanding the distribution of these vulnerabilities helps organizations in different sectors assess their risk and implement targeted security measures.
Web Applications: 35% of CVEs
Keywords: web application vulnerabilities, CVE impact, web security
Web applications accounted for 35% of the CVEs with a CVSS score of 10 in 2024. As businesses increasingly rely on web applications, securing these platforms becomes critical. Attackers often target web applications to steal sensitive data, deface websites, or deploy malware. CVE with CVSS Score 10.
Enterprise Solutions: 25% of CVEs
Keywords: enterprise solutions, CVE impact, critical infrastructure security
Enterprise solutions made up 25% of the CVEs with a CVSS score of 10. These solutions include software and systems used by businesses to manage operations, data, and communications. A vulnerability in enterprise solutions can lead to significant disruptions, data breaches, and financial losses.
IoT Devices: 20% of CVEs
Keywords: IoT security, device vulnerabilities, connected devices
IoT devices accounted for 20% of the CVEs with a CVSS score of 10. The growing number of connected devices increases the attack surface for cybercriminals. IoT vulnerabilities can allow attackers to gain control of devices, disrupt operations, or access sensitive data.
Other Categories: 20% of CVEs
Keywords: miscellaneous vulnerabilities, cybersecurity threats, sector analysis
The remaining 20% of CVEs with a CVSS score of 10 fell into other categories. These could include vulnerabilities in networking equipment, operating systems, or other software not classified under the previous categories. Organizations must remain vigilant across all potential attack vectors.
Detailed Analysis of Key CVEs in 2024
Keywords: detailed CVE analysis, cybersecurity trends, vulnerability case studies
This section provides an in-depth analysis of some of the most critical CVEs identified in 2024. Understanding these specific vulnerabilities helps organizations learn from real-world examples and implement effective security measures.
Web Application Zero-Day Exploit
Keywords: zero-day exploit, web application security, critical vulnerability
In January 2024, a zero-day exploit in a popular web application platform was discovered. This vulnerability allowed attackers to execute arbitrary code remotely. The exploit was particularly dangerous because it required no authentication, allowing any user to trigger the vulnerability.
Enterprise Resource Planning (ERP) Software Vulnerability
Keywords: ERP vulnerability, enterprise security, data breach risk
In March 2024, a critical vulnerability in an ERP system used by many large enterprises was identified. This CVE allowed attackers to gain unauthorized access to the system, potentially leading to data breaches and operational disruptions.
IoT Device Backdoor
Keywords: IoT backdoor, connected device security, remote access
A backdoor vulnerability in a widely-used IoT device was disclosed in April 2024. This vulnerability allowed attackers to remotely control the device, potentially leading to network disruptions or unauthorized data access.
Common Themes and Trends in 2024 CVEs
Keywords: cybersecurity trends, vulnerability patterns, common attack vectors
Several common themes emerged in the 2024 CVEs with a CVSS score of 10. Understanding these trends helps organizations anticipate future threats and refine their security strategies.
Increasing Complexity of Exploits
Keywords: exploit complexity, advanced threats, cybersecurity challenges
Exploits are becoming more complex, making them harder to detect and mitigate. Attackers are using sophisticated techniques to bypass security measures and achieve their objectives. This trend underscores the need for advanced security solutions and continuous monitoring.
Targeting of Critical Infrastructure
Keywords: critical infrastructure, targeted attacks, sector-specific vulnerabilities
Many CVEs in 2024 targeted critical infrastructure, including energy, finance, and healthcare sectors. These attacks highlight the importance of securing essential services that underpin society.
Growth of IoT-Related Vulnerabilities
Keywords: IoT growth, device vulnerabilities, cybersecurity risks
The proliferation of IoT devices has led to an increase in related vulnerabilities. As more devices connect to the internet, securing these endpoints becomes a significant challenge for organizations.
Best Practices for Managing CVEs with a CVSS Score of 10
Prioritizing Patching and Updates
Keywords: patch management, vulnerability remediation, software updates
Organizations must prioritize patching and updates for vulnerabilities with a CVSS score of 10. Promptly applying patches reduces the window of opportunity for attackers to exploit these critical vulnerabilities.
Implementing Comprehensive Monitoring and Detection
Keywords: monitoring, threat detection, cybersecurity tools
Continuous monitoring and detection are essential for identifying and responding to security incidents. Implementing tools that provide real-time visibility into network activity helps detect potential exploits before they cause harm.
Conducting Regular Security Audits and Assessments
Keywords: security audits, risk assessment, vulnerability management
Regular security audits and assessments help identify potential vulnerabilities before they are exploited. These audits should include both internal systems and third-party software used by the organization.
Employee Training and Awareness
Keywords: cybersecurity training, employee awareness, human factors
Employee training is crucial for preventing security incidents. Educating staff about cybersecurity best practices, social engineering tactics, and the importance of regular updates helps reduce the risk of exploitation.
Developing Incident Response Plans
Keywords: incident response, crisis management, cybersecurity strategy
An incident response plan outlines the steps an organization should take in the event of a security breach. Developing and regularly updating these plans ensures that the organization can respond effectively to mitigate damage.
Engaging with Cybersecurity Experts
Keywords: cybersecurity experts, professional guidance, security partnerships
Partnering with cybersecurity experts provides organizations with the specialized knowledge needed to address complex vulnerabilities. These experts can offer guidance on best practices, advanced security solutions, and emerging threats.
Conclusion
In 2024, the cybersecurity landscape saw a significant number of CVEs with a CVSS score of 10. These critical vulnerabilities spanned various sectors, including web applications, enterprise solutions, and IoT devices. The increasing complexity of exploits and the targeting of critical infrastructure highlight the need for robust security measures. Organizations must prioritize patching, implement comprehensive monitoring, conduct regular audits, and train employees to manage these vulnerabilities effectively. For expert guidance on addressing these critical security challenges, contact Hyper ICT Oy in Finland. Our team of professionals is equipped to help you protect your organization from the most severe cybersecurity threats. CVE with CVSS Score 10.
Contact Hyper ICT


